The Mouse That Knows You
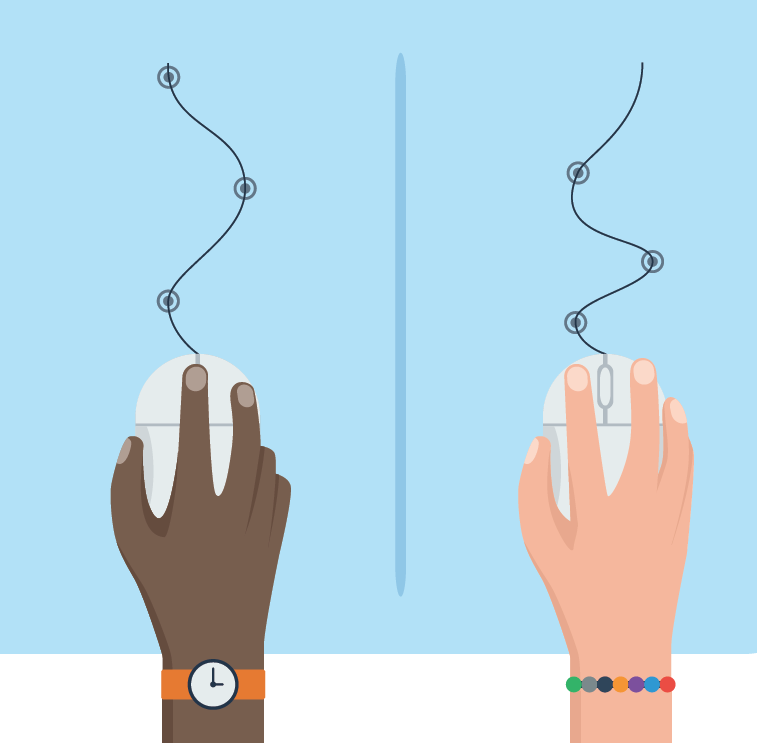
Like a fingerprint, unique mouse movements could protect your personal information. Kamal Rangavajhula, a Master of Science in Management Information Systems (MIS) candidate, conducted research using behavioral biometrics.
The Mouse That Knows You | Hood Magazine, Spring 2019
If a computer user forgets to log out of a bank account or email, or a hacker steals credentials, the user’s personal information could be compromised. An increasingly popular way to enhance account security is the use of behavioral biometrics—or data collected from a user’s mouse movements or keyboard strokes—including how fast a double-click is, how fast the mouse scrolls, angle and speed of drag-and-drop activity, and time between keystrokes.
A software program builds a profile of the user and continuously compares it with current mouse and keyboard action. If the system detects an anomaly—an action indicating a different person is using the computer—it logs out or otherwise limits the account on the user’s behalf. Whereas logging into an account is a one-step verification process, behavioral biometrics verify the user continuously, several times per second.
Graduate candidate Kamal Rangavajhula presented on this topic at Hood’s 2018 Three-Minute Thesis (3MT) Competition and won the event’s People’s Choice Award. This competition, founded in 2008 by the University of Queensland in Australia, challenges graduate students to present their research projects in three minutes using just one PowerPoint slide. Rangavajhula’s presentation, “Detection of Unauthorized Mouse Movements Using Mouse Dynamics,” showed that, using an Extreme Gradient Boosting algorithm, this technology can detect anomalies with an accuracy rate of 99.49 percent.
Behavioral biometric technology is rapidly evolving. It began in banking to prevent fraud, but its uses will continue to expand along with the markets that will adopt it. BioCatch, a leader in behavioral biometric software, says behavioral biometrics are starting to be used to authenticate a person’s identity before issuing account credentials, and by companies as part of their strategy to reduce unauthorized access to IT and data. This technology is expanding to markets including e-commerce, credit card issuers, credit bureaus, payroll systems, gaming, device authentications and enterprise, and it is expected to become the most important authentication factor for mobile and web. BioCatch also expects traditional biometrics, such as fingerprints and voice recognition, to combine with behavioral biometrics to create more secure systems.
Mouse Dynamics and Behavioral Biometrics in the Real World
Behavioral biometrics are used most notably in banking security, collecting user activity data, government and health care.
A New York Times article reported that the Royal Bank of Scotland records more than 2,000 interactive gestures to build customer profiles using software from BioCatch. The profile is then compared against the customer’s movements every time they return. The system accurately detects imposters 99 percent of the time.
In one case, “the software picked up unusual signals coming from one wealthy customer’s account. After logging in, the visitor used the mouse’s scroll wheel—something the customer had never done before. Then the visitor typed on the numerical strip at the top of a keyboard, not the side number pad the customer typically used. Alarm bells went off. The R.B.S. system blocked any cash from leaving the customer’s account. An investigation later found that the account had been hacked.”
According to the Daily Dot, Facebook tracks mouse movements to determine if users are humans or bots, and to determine if the user’s Facebook window is in the foreground or background. This tells the company if users are actually browsing the site or just have it open with other tabs. ■
Future Data Scientist
Kamal Rangavajhula will graduate in May with a Master of Science in Management Information Systems (MIS). After earning his bachelor’s degree in electronics and telecommunications engineering from Andhra University in India, he started looking for academic programs that could bridge the gap between the information technology and management fields. He found MIS at Hood, saw the curriculum reflected the technologies in the current market, and applied to the program.

In his first semester, Rangavajhula took Introduction to Data Analytics/Mining with Professor Carol Jim, Ph.D. where he learned the critical role of data for an organization to survive in the 21st century. He then taught himself R programming and Python, two programming languages for data analytics. In his second semester, discussions with Professor Ahmed Salem, Ph.D. and Professor Jim about pursuing a career in data science led to his research and 3MT presentation.
Rangavajhula currently has an internship at Lendeavor, a Silicon Valley financial-technology startup, where he updates listings in the company’s database, contacts new brokers and brainstorms with the software engineering team to enhance the user experience for customers on Lendeavor’s website. He plans to pursue a career in exploratory data science, figuring out how to use data effectively to achieve business goals.
Are you ready to say Hello?
Choose a Pathway
Information will vary based on program level. Select a path to find the information you're looking for!
